Scenario Description
In the context of security compliance, IT departments often implement policies for regularly changing server passwords to protect data. For example, administrators may update passwords for critical servers every three months. This practice reduces security risks associated with former employees' access and prevents hackers from obtaining passwords through brute force attacks. JumpServer offers a <Change account secret> feature that allows for scheduled password changes, recording the process for auditing purposes. This not only ensures system security but also supports future audits, helping organizations maintain data security effectively.
Function Description
The password change feature currently supports changing passwords for assets using the SSH protocol, such as servers and databases. However, it does not support changing Windows domain account passwords.
This feature is designed to meet users' security needs by allowing regular password updates for users on assets, reducing manual operations.
Password changes are performed by configuring privileged account options for the asset within JumpServer.
Operation Instructions
For example, using a Linux host.
Change the root account
Since the root account has high privileges, if there is a need to change the root password, you need to add the parameter <CHANGE_AUTH_PLAN_SECURE_MODE_ENABLED=false> in the JumpServer configuration file </opt/jumpserver/config/config.txt> to allow JumpServer to change the root password. After configuration, restart the JumpServer service for the changes to take effect.
echo "CHANGE_AUTH_PLAN_SECURE_MODE_ENABLED=false" >> /opt/jumpserver/config/config.txtCreate account secret change task
Switch to the JumpServer Console page, click <Automations>, then click <Change account secrets> to access the Task page, and click <Create> to create a new task.
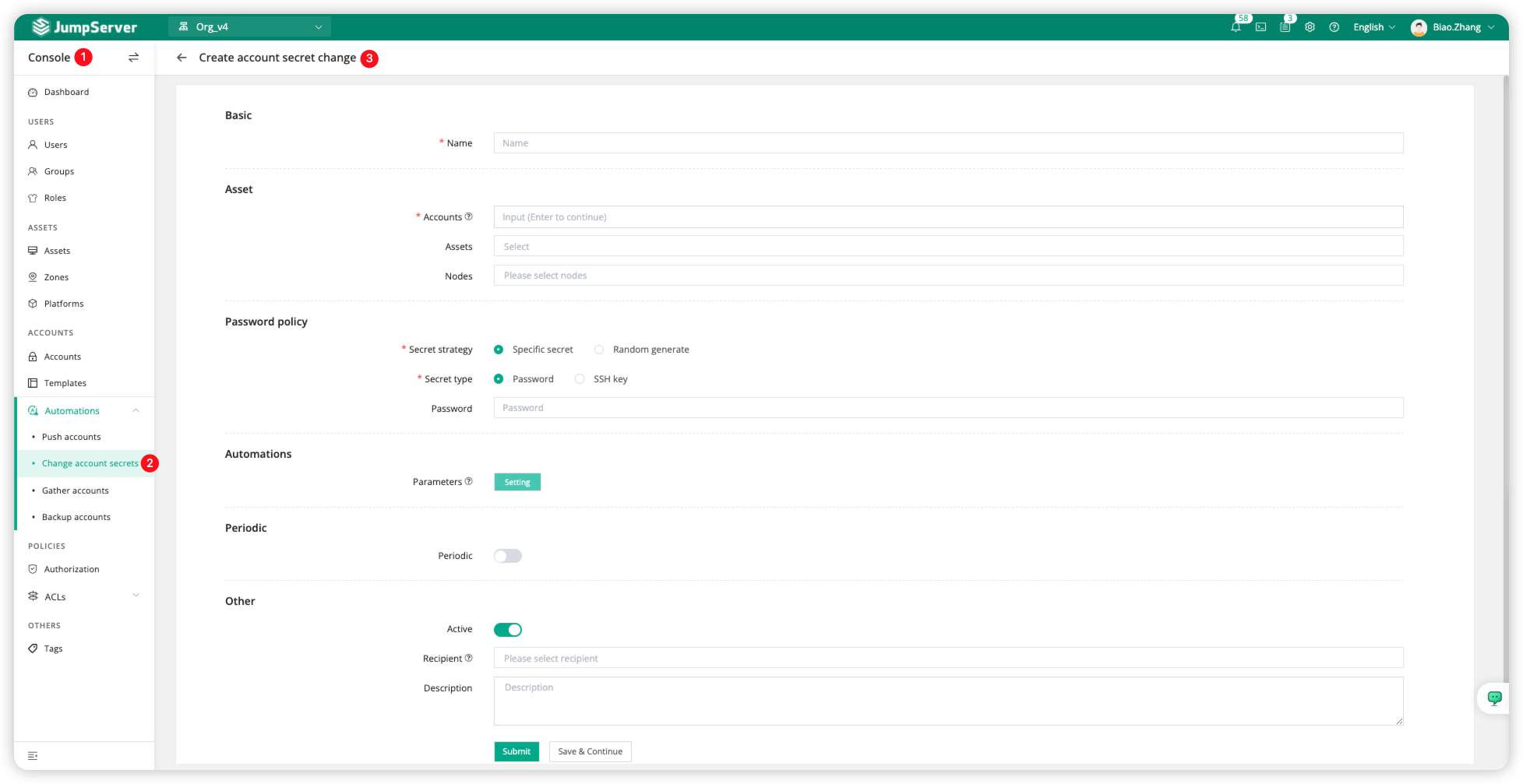
On the current page, we can configure the password change rules, including the Accounts and Assets involved, and we can also select all assets under the nodes (Nodes). Additionally, we need to customize the Password policy and Periodic-related information.
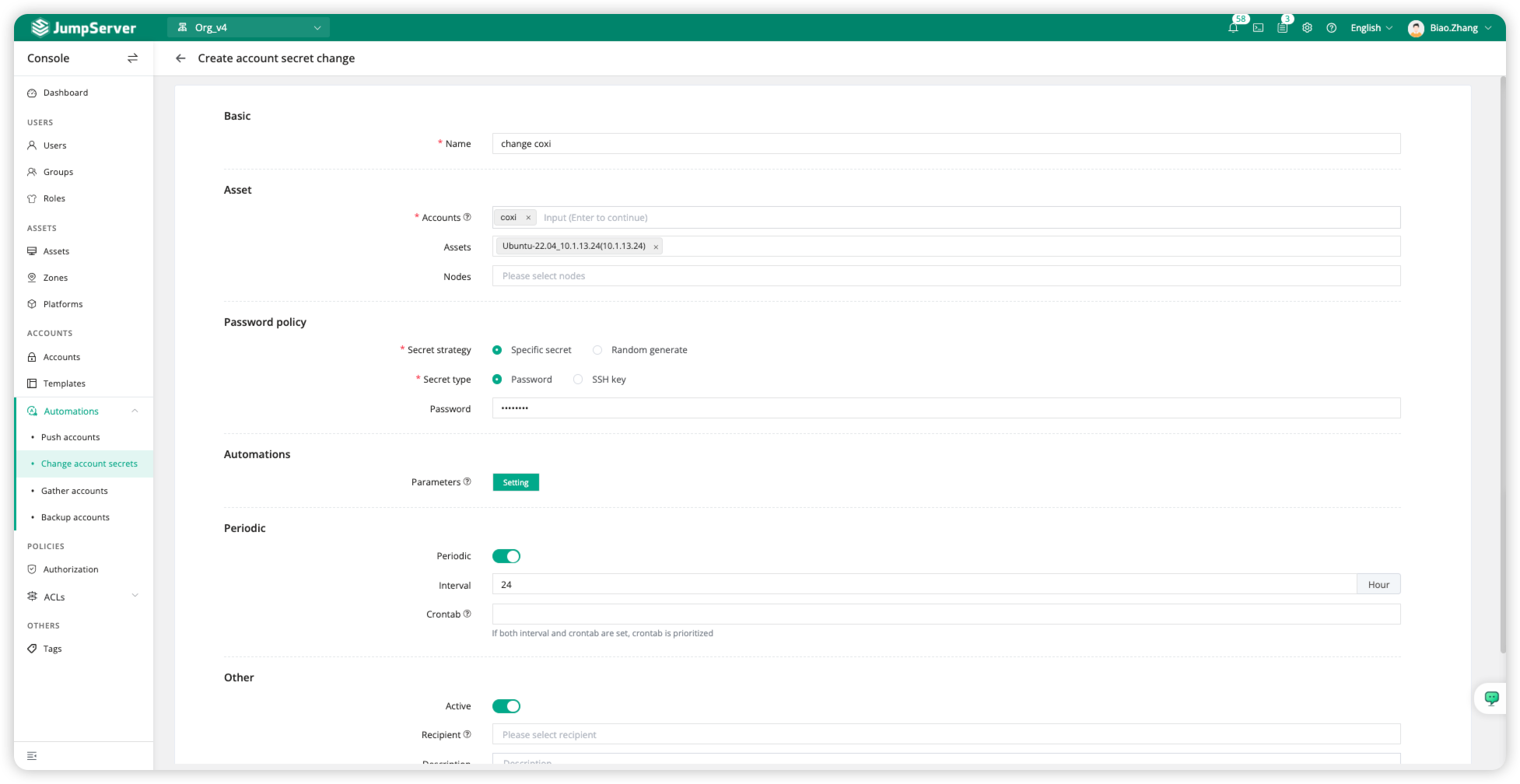
Detailed Parameter Description:
Click <Assets> to switch to the asset page, select the asset name, and then click <Accounts> again. Here, we can use the <Privileged> field to confirm whether there are privileged accounts in our assets. Privileged accounts must be high-privilege accounts, which is one of the necessary conditions for password change.
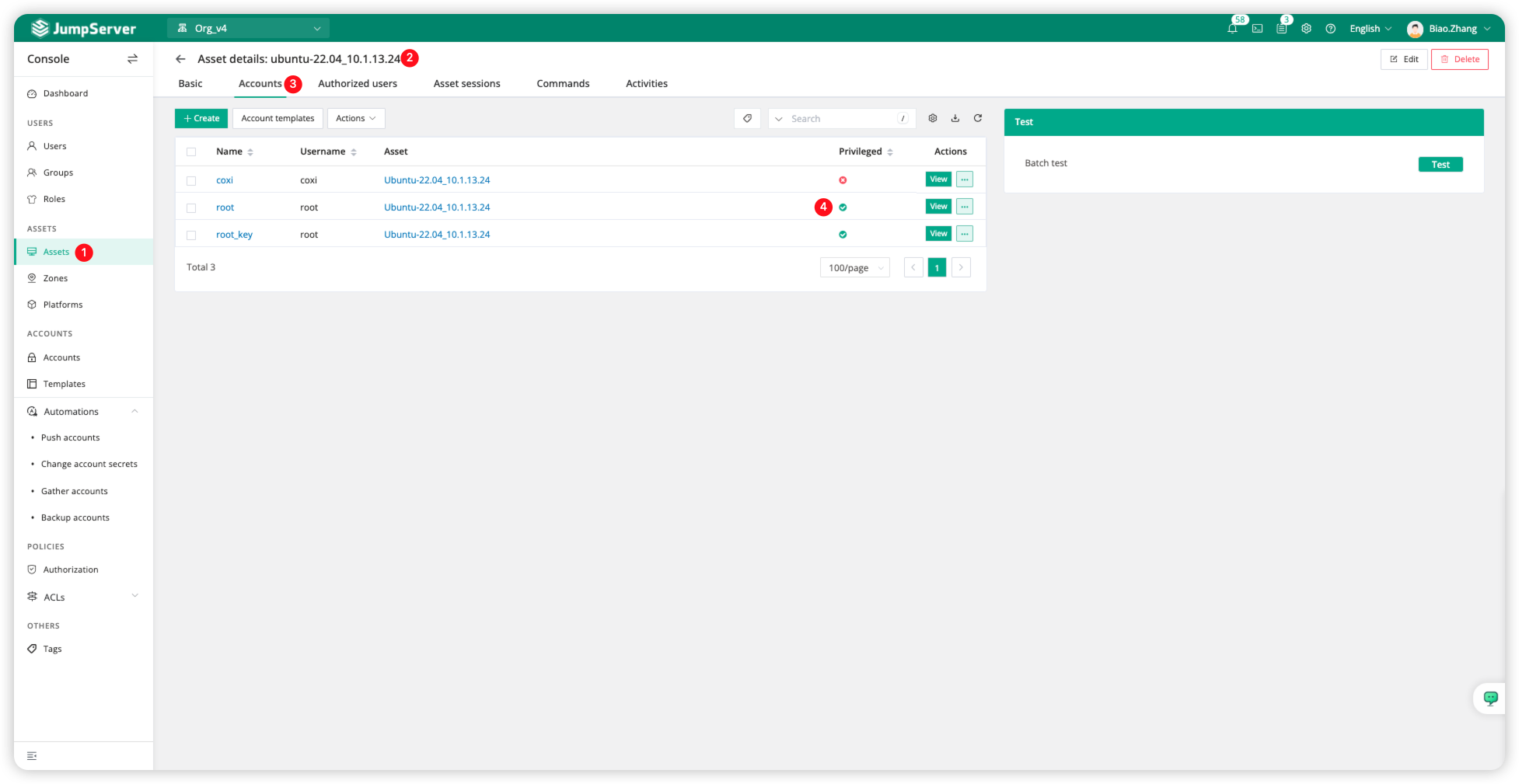
Execute account secret change task
Select the <Actions> field of the password change task and click <Execute> to manually execute the task.
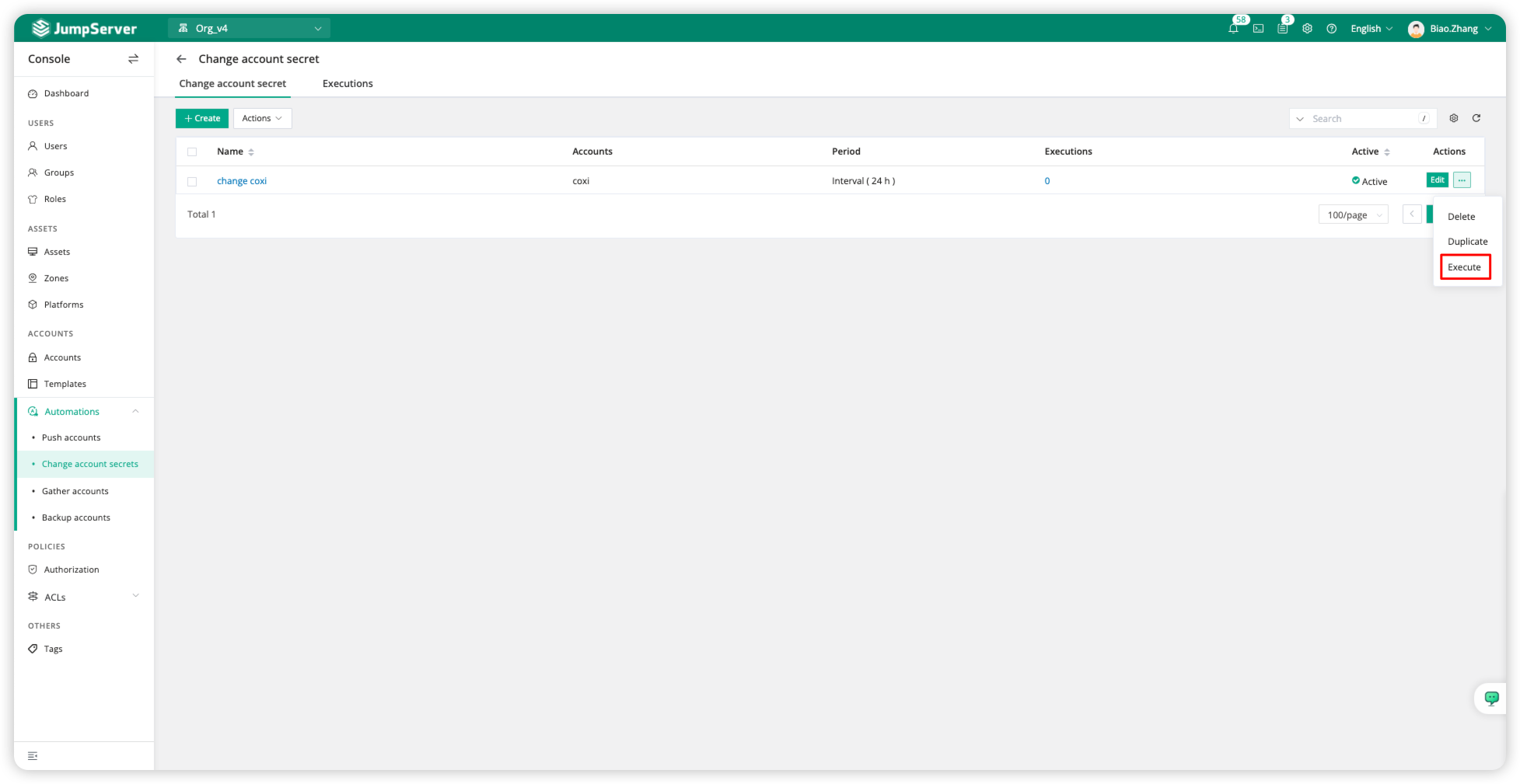
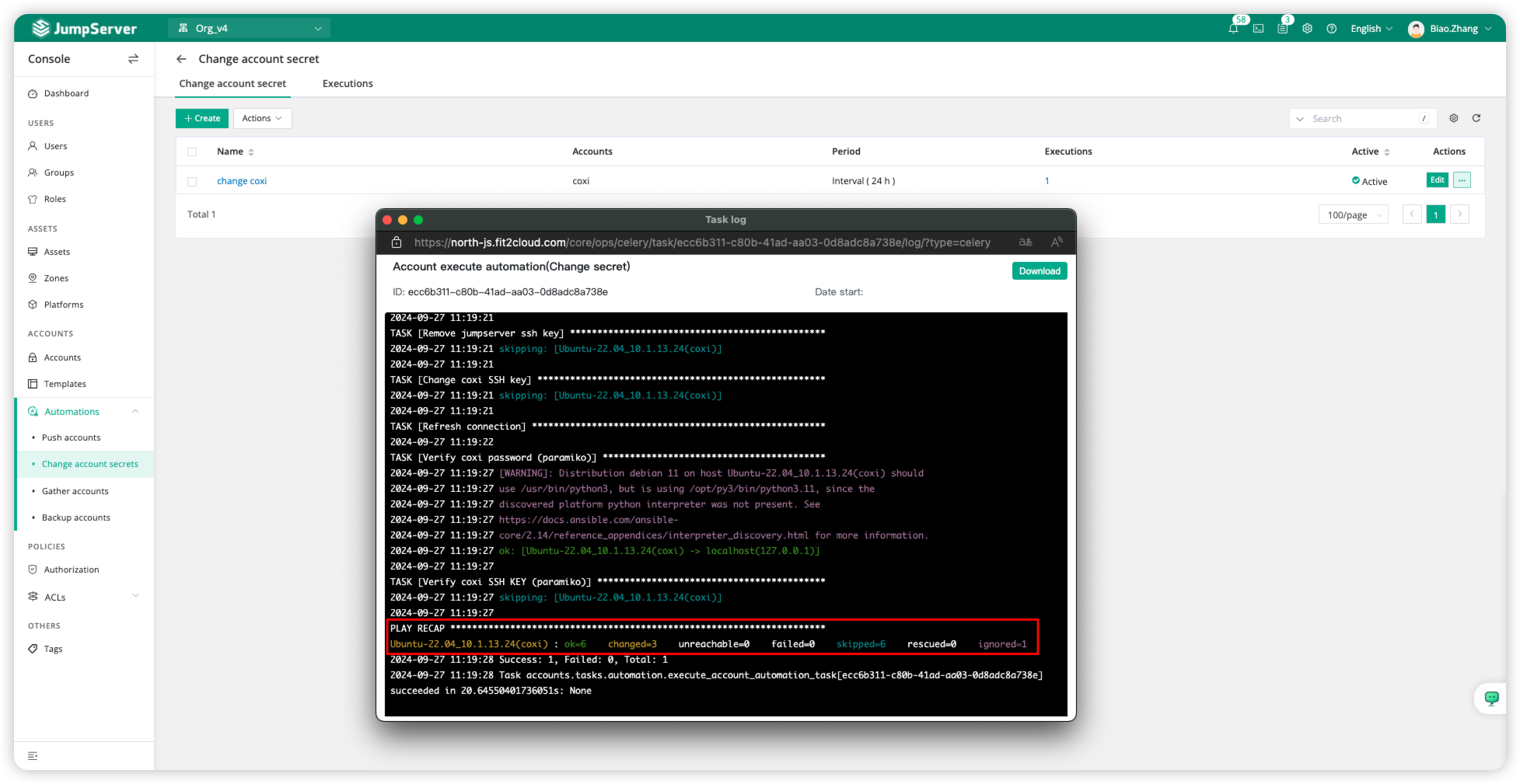
During execution, it typically includes operations such as Test privileged root account, sudo setting, and change password as conditions for modifying the account. After completion, we can determine the task result by checking statuses like ok or Success.
Function Verification
Here, we will verify the results of the password change.
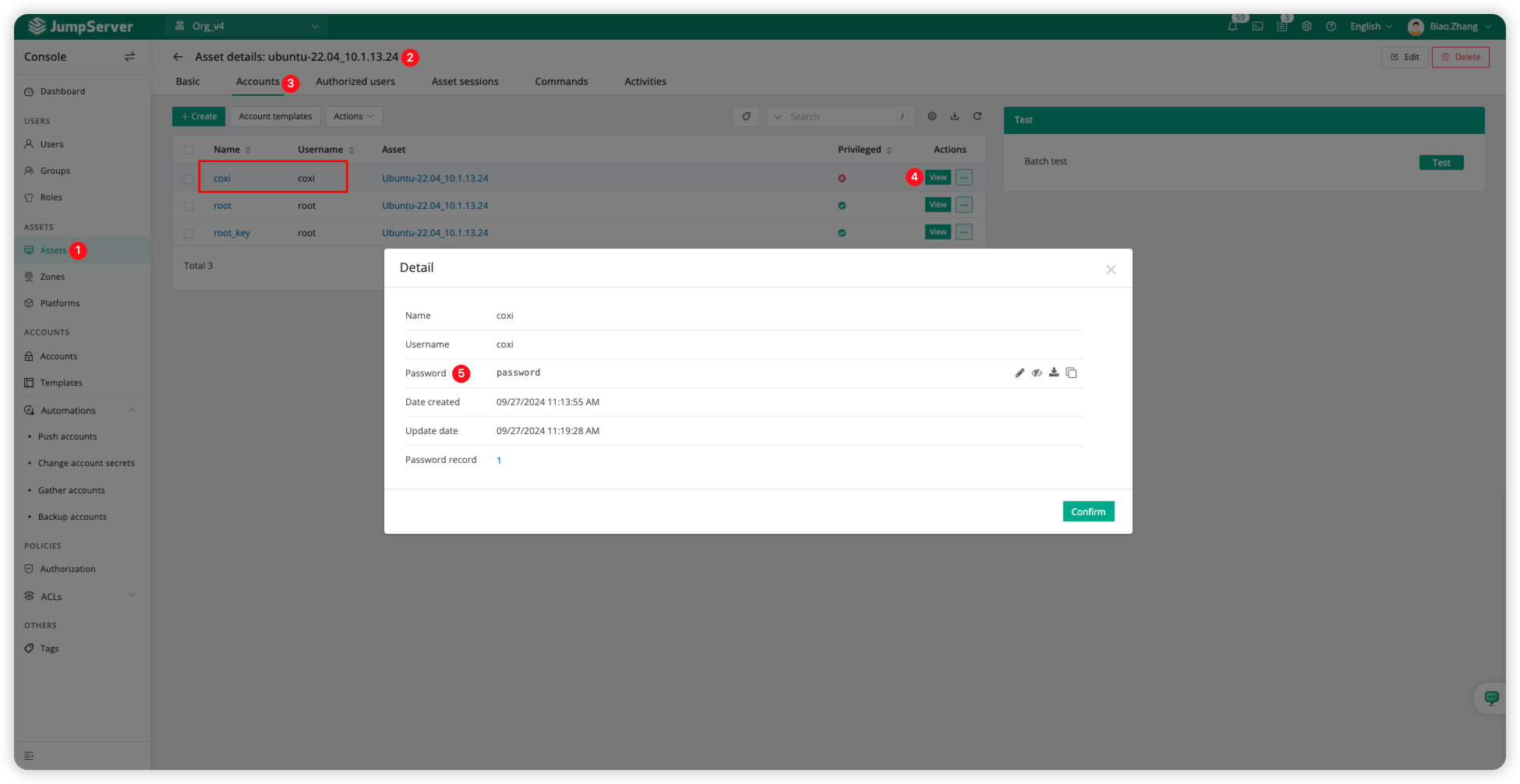
Check the password after the change
Click <Assets> to switch to the asset page, select the asset name, and click <Accounts> again. Here, we can click the <View> button for the changed password account to see the current password, which is configured as "password" in the password change plan for verification. To view the password securely, MFA authentication is required.
Asset connection
We switch to the Web Terminal page, select the account that has been changed, and successfully connect to the asset.