As a global leader in power technology, Cummins (China) Investment Co., Ltd. (hereinafter referred to as Cummins China) designs, manufactures, and distributes diverse power solutions while providing service support. The company’s products include diesel and natural gas engines, generator sets, alternators, emission treatment systems, turbocharging systems, fuel systems, control systems, transmissions, braking technologies, axle technologies, filtration systems, as well as hydrogen production, storage, and fuel cells.
Cummins was founded in 1919, with its headquarters in Columbus, Indiana, USA. The company employs approximately 59,900 people globally and is the world’s largest independent engine manufacturer. Cummins operates over 10,600 certified dealer locations and more than 500 distribution service centers worldwide, providing products and support to customers in more than 190 countries and regions. In 2022, the company achieved $28.1 billion in sales revenue and $2.2 billion in net income.
Operational Security Audit Needs of Cummins China
As an engine manufacturing company, Cummins China has the following primary needs for operations security audits:
1. Compliance with Graded Protection Standards
To meet external security compliance requirements, Cummins China urgently needed to address enterprise data security issues through a bastion host. This involved building a comprehensive operations security audit platform to enable security managers to centrally manage users and resources, allocate permissions, and conduct audits. Furthermore, the entire operations management system must comply with relevant regulations and requirements under the Cybersecurity Law of the People’s Republic of China concerning information system security level protection.
2. Unified Access to Assets
Cummins China’s assets are primarily distributed across public cloud platforms such as Amazon AWS and Azure, connected to office networks via dedicated lines. Internal business systems (e.g., the e-Cummins app, SRM system, and IoT systems) are independently managed by various departments, resulting in non-unified access points that complicate management. To simplify the unified management of assets, Cummins China sought to build a unified operations security audit platform to provide a single access point for all assets, ensuring a unique operational path.
3. Integration with User Systems and Single Sign-On
Currently, Cummins China’s business systems use Microsoft Azure AD for unified identity authentication and OpenID for single sign-on (SSO). To meet unified management requirements, the bastion host was required to integrate with both AD and OpenID, allowing centralized user identity authentication to achieve unified and centralized user management.
4. Independent Departmental Management and Auditing
Cummins China has multiple internal departments, each independently managing their assets and personnel permissions. Through the bastion host, the company aimed to centralize asset and personnel management while meeting the needs for independent management and auditing at the departmental level, as well as unified management and auditing at the corporate level.
Bastion Host Selection Process
Based on the above needs, Cummins China began searching for suitable bastion host solutions in the market. After extensive comparisons and testing, Cummins China chose JumpServer to build a unified operations security audit platform. The advantages of JumpServer include:
1. Rich 4A Functionality
As a widely adopted open-source bastion host, JumpServer provides powerful “4A” (Authentication, Accounting, Authorization, and Auditing) capabilities, enabling Cummins China to build an operations security audit platform that complies with graded protection standards.
2. Ease of Installation and Maintenance
JumpServer is easy to install, supporting both online and offline deployment methods, with straightforward maintenance. For version upgrades, JumpServer offers seamless backward compatibility and one-click script-based upgrades, either online or offline, ensuring zero-barrier operation.
3. Great User Experience
JumpServer supports both B/S and C/S architectures, allowing users to access assets directly through a browser without requiring additional plugins. It caters to diverse user needs, including development, operations, and database administration (DBA). Its clear interface layout and simple functionality ensure that even first-time users can quickly get started without incurring additional learning costs, making it easy to use and operate.
4. Flexible and Scalable Architecture
JumpServer adopts a modular design, decoupling the core and node deployments to ensure functionality decoupling. It supports containerized deployment or operation within a container platform, allowing unlimited scaling as assets and concurrency increase. Additionally, JumpServer supports various deployment schemes, including single-machine, active-passive, active-active, and distributed, meeting the diverse needs of different business scenarios.
JumpServer Deployment Architecture
To ensure high availability and user experience, Cummins China adopted a high-availability architecture design to maintain the continuous and stable operation of its business and application systems. Considering the future expansion of its IT infrastructure and growing IT asset scale, the system was designed with horizontal scalability. The high-availability architecture also supports adding frontend application nodes at any time to enhance the system’s support capacity further. The JumpServer deployment architecture of Cummins China is shown in Figure 1.
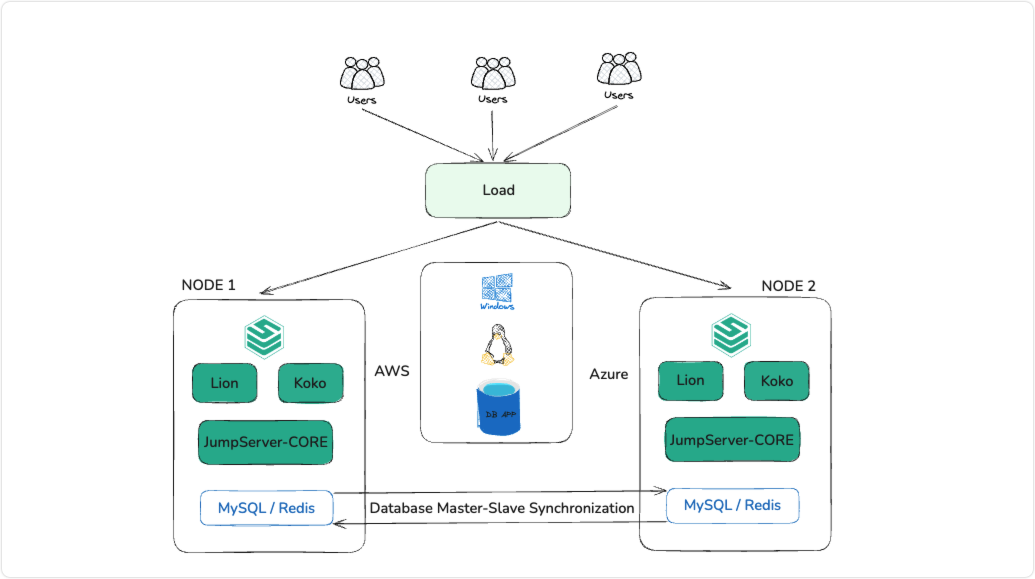
▲ Figure 1: Cummins China’s JumpServer Deployment Architecture
This deployment architecture provides a unified domain name and uses frontend load balancers to distribute user requests, achieving load balancing while automatically monitoring backend nodes. In addition to application high availability, MySQL and Redis are deployed in high-availability configurations to ensure uninterrupted database services and prevent data loss. This architecture not only meets the high-availability requirements of bastion host services but also flexibly accommodates the continuous growth of assets and user concurrency.
JumpServer Practical Scenarios
■ Multi-Tenant Management Model
JumpServer supports multi-tenant management by segmenting organizations to isolate resources and permissions between them. This allows for independent management and auditing by different organizations. Under a unified management and audit framework, administrators can segment business departments and assign specific organizational administrators to manage members, authorize assets, and define permissions within their organizations, greatly improving operational efficiency.
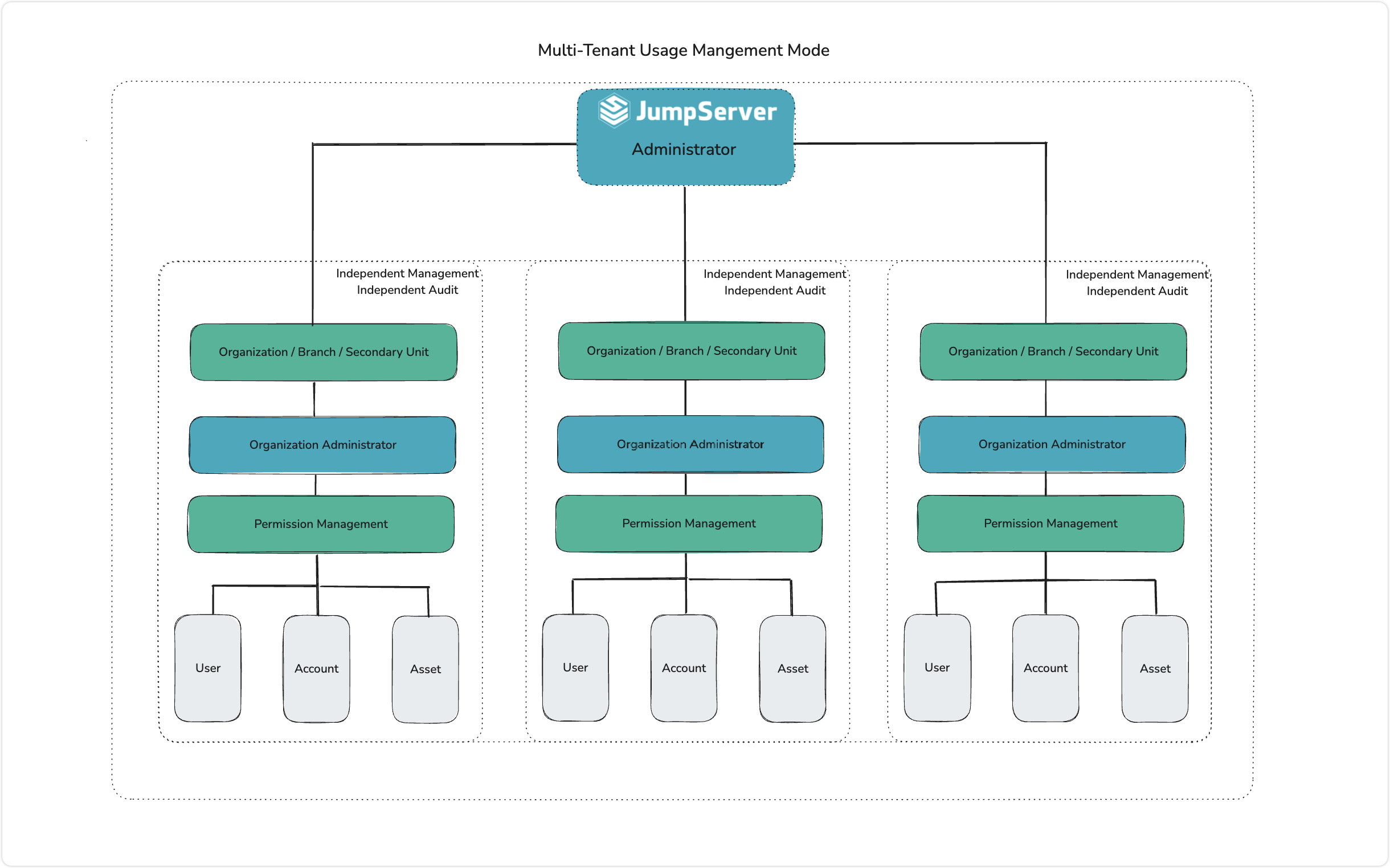
▲ Figure 2: JumpServer Multi-Tenant Management System
■ Unified Database Asset Management
Beyond general asset management, JumpServer supports direct integration with databases such as MySQL, PostgreSQL, Oracle, and SQL Server. It also supports multiple connection methods, including Web CLI, Web GUI, and direct database proxy connections, effectively meeting diverse database connection needs.
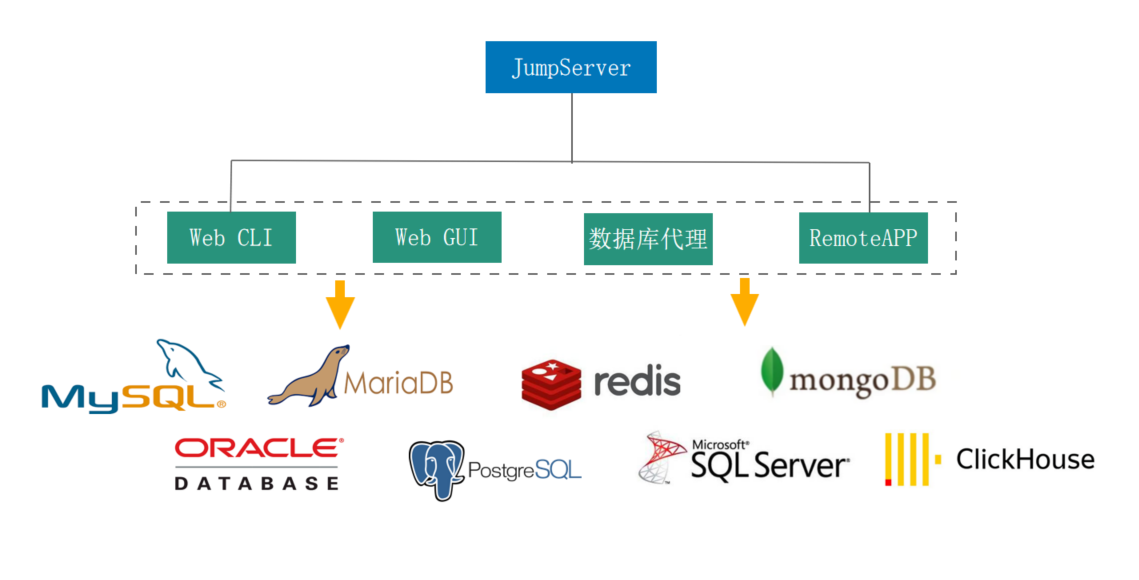
▲ Figure 3: JumpServer Supporting Various Database Management
■ Unified Management of Cross-VPC Assets
Cummins China’s assets are mainly hosted on public cloud environments like AWS and Azure. To meet business needs, the company has multiple VPC environments, but VPC assets cannot directly communicate with the JumpServer network. JumpServer supports domain gateways, enabling connection with VPC assets through proxy methods, achieving unified management of cross-VPC assets.
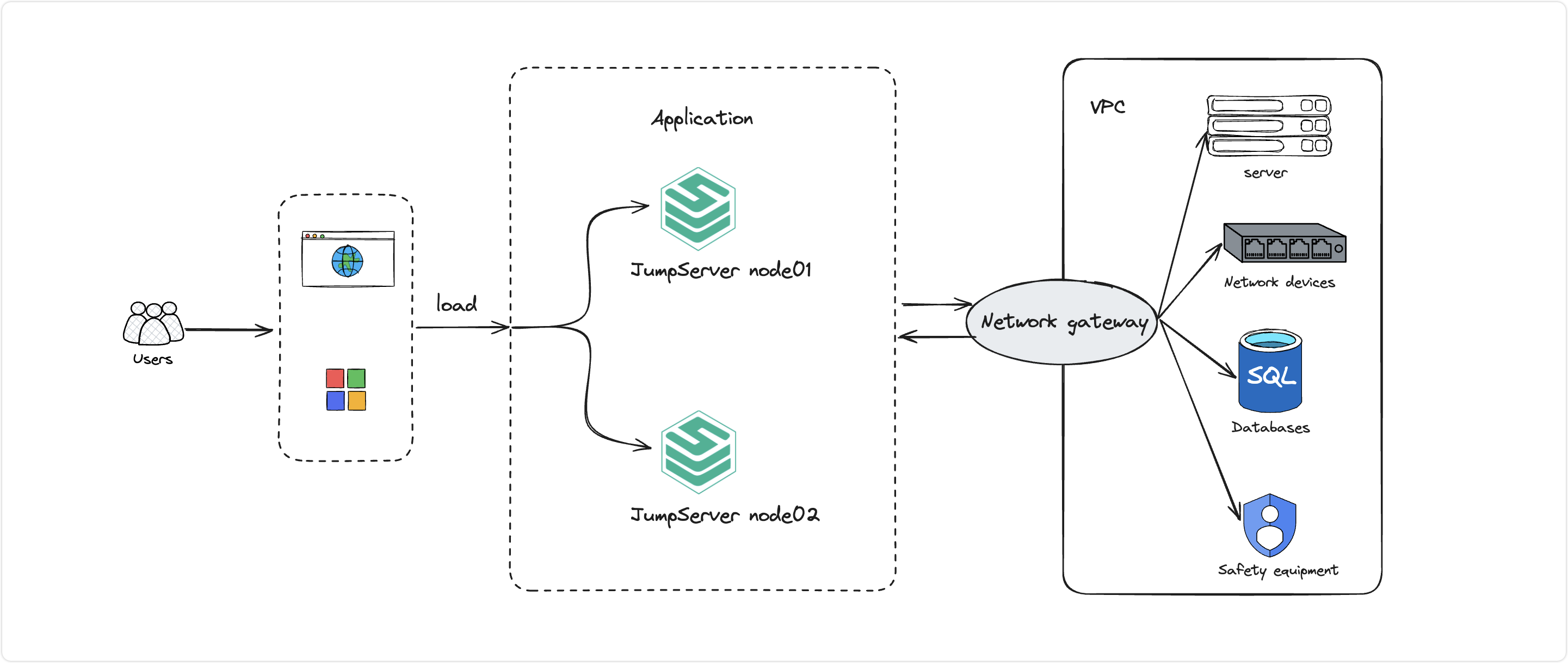
▲ JumpServer Supports Cross-VPC Resource Management
■ User Request Distribution via Endpoint Rules
JumpServer supports endpoint rules to designate specific access nodes for particular assets. Endpoints are the addresses (ports) used by users to access services. When a user connects to an asset online, the system selects an appropriate endpoint based on the rules and asset tags to establish a connection, enabling distributed asset access.
Note: If asset IPs conflict under different endpoints, asset tags can be used to resolve the issue.
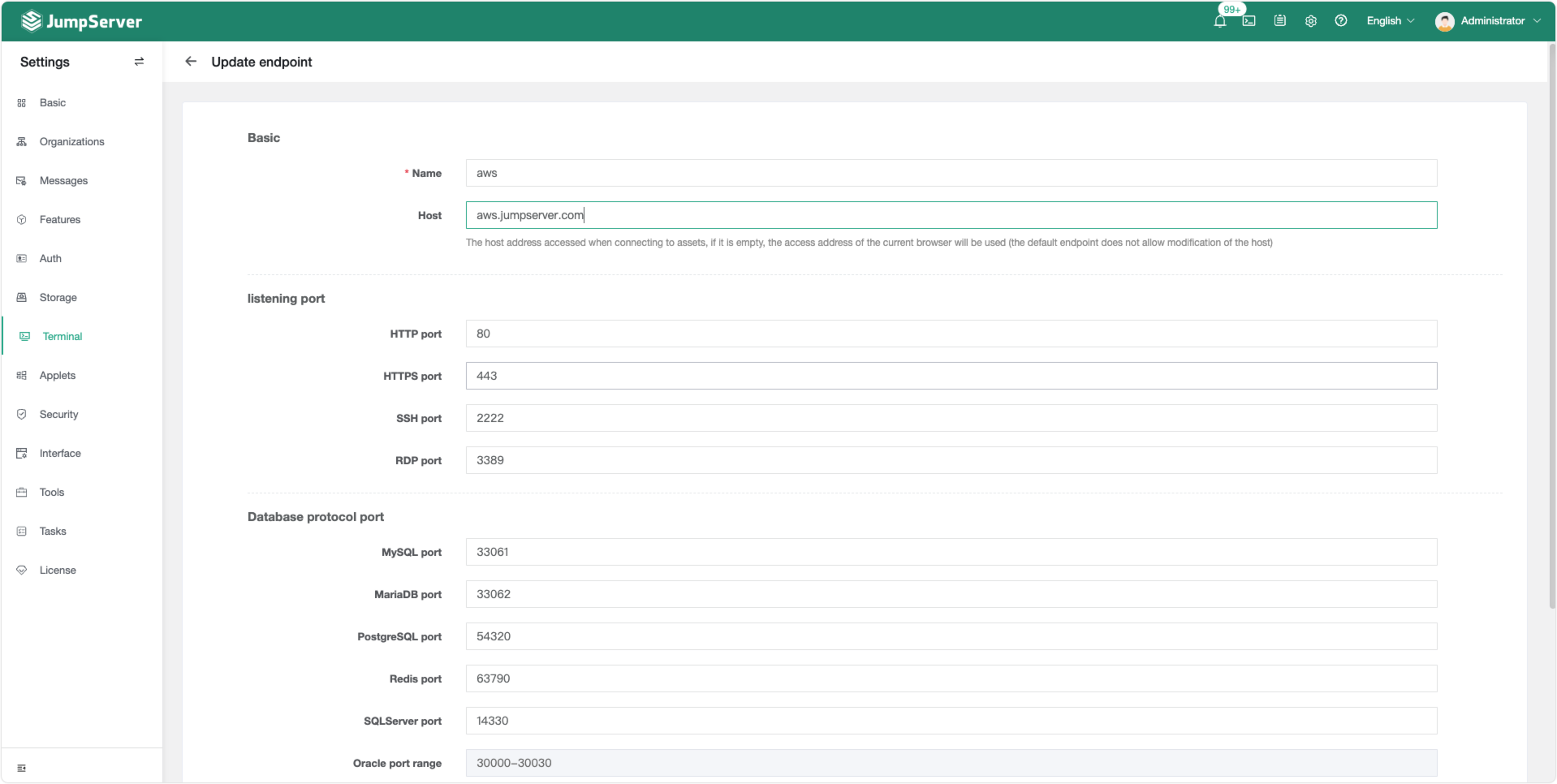
▲ Example: Configuring JumpServer Endpoints
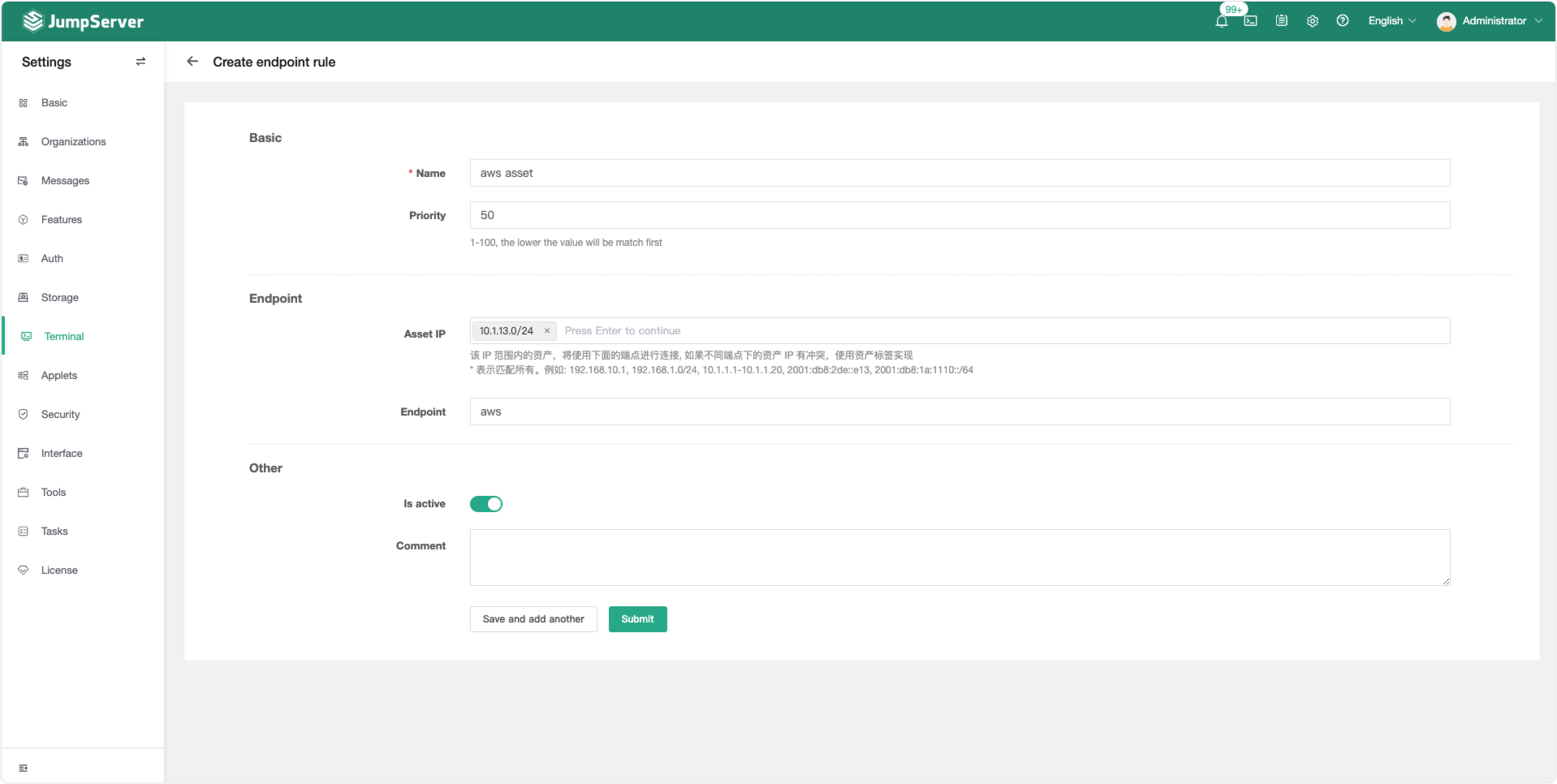
▲ Example: Setting JumpServer Endpoint Rules
Value of Using JumpServer
Business Value Gained by Cummins China from Deploying and Using JumpServer
■ Compliance with Graded Protection Standards JumpServer enables administrators to promptly initiate cybersecurity emergency response plans, investigate and assess incidents, and take appropriate technical measures to eliminate security risks.
■ Centralized IT Asset Management JumpServer centralizes access and management of cloud servers, Linux servers, Windows servers, and databases. It provides a single secure access channel, effectively controlling user operations and preventing direct access to critical resources.
■ Improved Operational Efficiency While ensuring overall system security, Cummins China achieved independent departmental management and auditing through JumpServer’s multi-tenant model, meeting both independent and unified management requirements. This improved operational efficiency while enhancing the overall security mechanism.
